Configuring AD/LDAP Integration for User Authentication
In this chapter, you’ll learn how to configure Nectus to work with Microsoft Active Directory and the LDAP protocol for user authentication.
The specific topics we will cover in this chapter are:
- What are AD and LDAP?
- Why Configure Nectus Integration with AD/LDAP?
- How Nectus Authenticates Users
- Connecting Nectus to an LDAP Server
- Mapping AD/LDAP Groups to Local User Groups
- Mapping AD/LDAP Users to Local User Groups
1. What are AD and LDAP?
AD stands for Active Directory Domain Services. It is a Microsoft service that provides authentication and other services to devices on a network. It is an LDAP compliant database of users, groups, and other objects.
LDAP stands for Lightweight Directory Access Protocol. It is an Internet standard for accessing distributed directory services. Nectus uses LDAP to communicate with AD.
2. Why Configure Nectus Integration with AD/LDAP?
Configuring Nectus to integrate with AD/LDAP simplifies user management for large organizations. Like most applications, Nectus has its own local user authentication database. But when a organization has many applications maintaining separate user accounts for each application isn’t practical.
The solution is to maintain user accounts in AD. Using LDAP, each application can query the AD database for the user authentication information it needs. This greatly simplifies user account maintenance.
3. How Nectus Authenticates Users
Nectus is designed to function on its own or integrated with AD/LDAP. Security settings are based on Local User Groups whether the User Account is stored locally, or in AD.
When a user logs in Nectus first checks to see if the active user has a Local User Account. If so, Nectus uses this account for the login.
Note: To manage the Nectus Local User Accounts and the Local User Groups go to the Nectus Home Screen and select Settings -> Admin Accounts. This opens the “Admin Accounts” dialog box. See the article, “Creating User Accounts and User Groups” for details.
If the active user does not have a Local User Account, Nectus checks to see if Active Directory integration is configured. If so, it checks to see if the active user has an account in AD.
If the user has an account in AD, and the user’s LDAP Group Name is mapped to a Local User Group, Nectus uses the Local User Group settings.
If there is no mapping to a Local User Group, Nectus checks to see if the active user’s LDAP Account Username is mapped to a Local User Group and uses those settings.
If none of the above is true, Nectus denies the user access.
Important: We recommend that you always maintain at least one Local User Account in Nectus to ensure access even if the AD/LDAP connection is down.
4. Connecting Nectus to an LDAP Server
To integrate Nectus with AD you need to configure the LDAP Server settings and enable LDAP.
To configure the LDAP Server settings and enable LDAP go to the Nectus Home Screen and select Settings -> LDAP Integration.
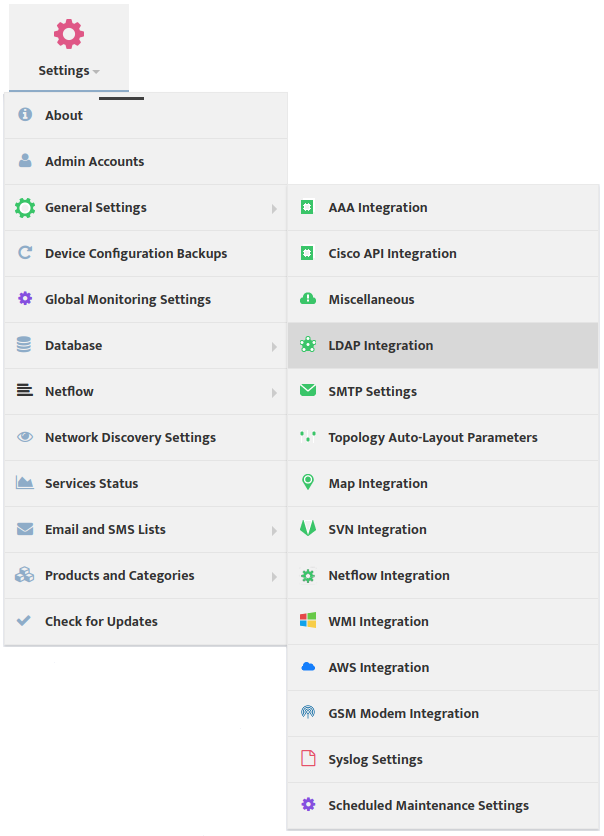
This opens the “LDAP Integration” dialog box.
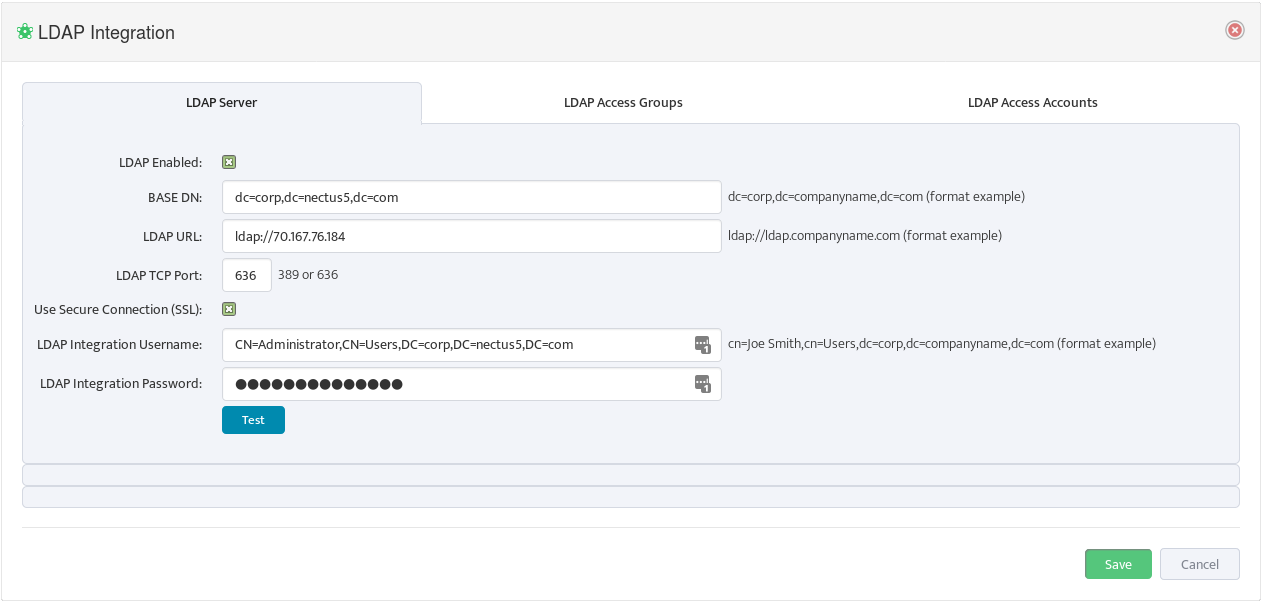
Select the LDAP Server tab and enter the LDAP parameters. You can see examples of the format for these parameters to the right of the relevant fields. Check LDAP Enabled.
5. Mapping AD/LDAP Groups to Nectus Local User Groups
Mapping an AD/LDAP Group to a Nectus Local User Group causes the entire AD/LDAP group to inherit the security settings from the Nectus Local User Group.
To map AD/LDAP Groups to Nectus Local User Groups, open the “LDAP Integration” dialog box and select the LDAP Access Groups tab.
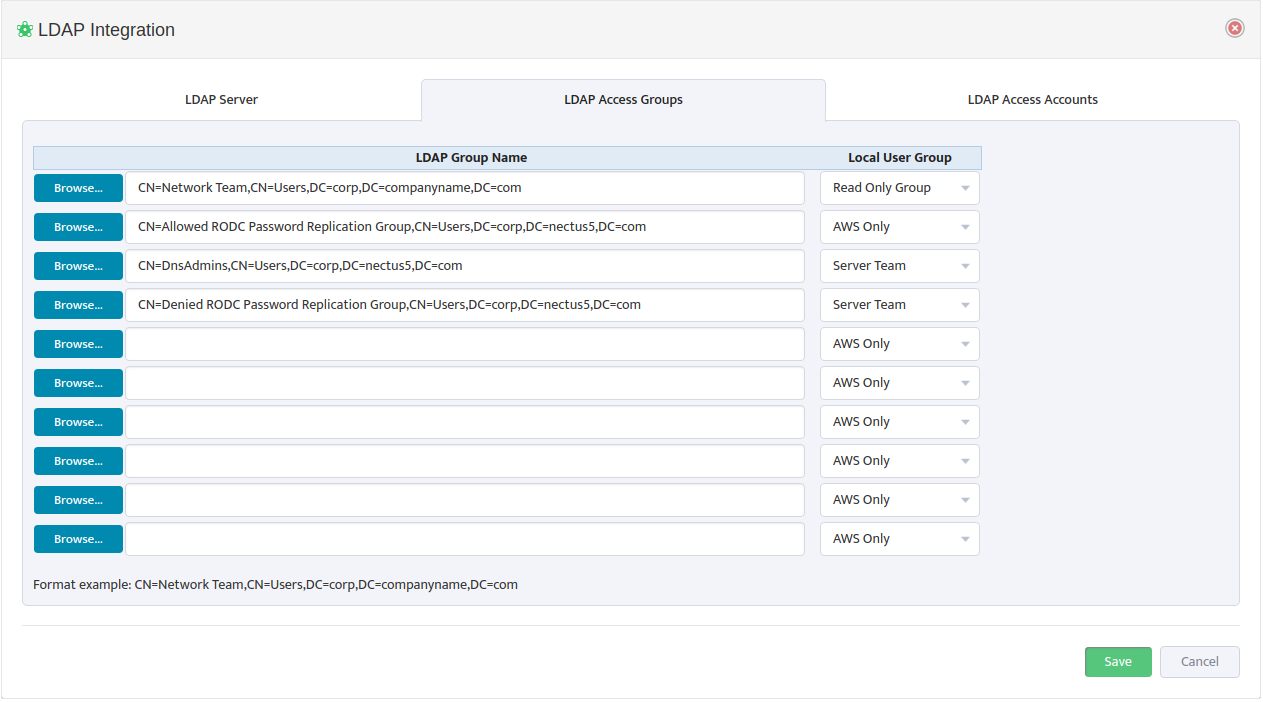
Use a Browse button on the left to open the “Select group from LDAP Server” dialog box and select an LDAP Group Name. 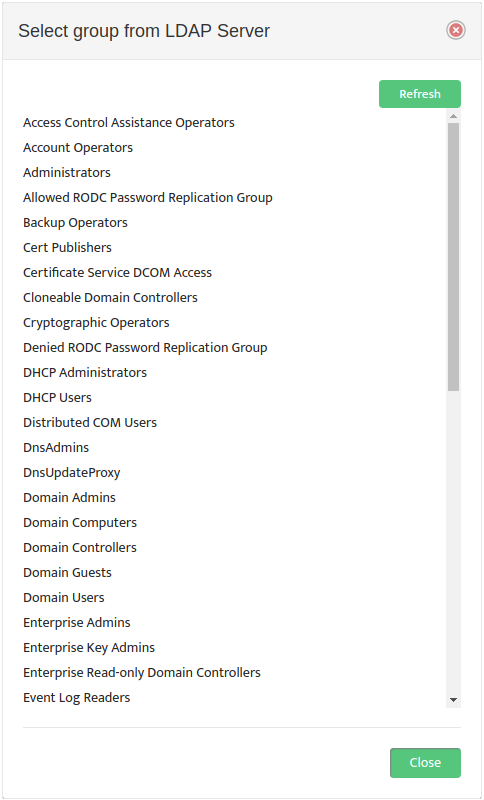
Nectus returns you to the “LDAP Integration” dialog box. In the drop-down list to the right of the LDAP Group Name, select the Local User Group to map it to. An example of the proper LDAP Group Name format appears at the bottom of the dialog box.
6. Mapping AD/LDAP Usernames to Nectus Local User Groups
Mapping an AD/LDAP Username to a Nectus Local User Group causes the specific AD/LDAP User to inherit the security settings from the Nectus Local User Group.
To map AD/LDAP Account Usernames to Nectus Local User Groups, open the “LDAP Integration” dialog box and select the LDAP Access Accounts tab.
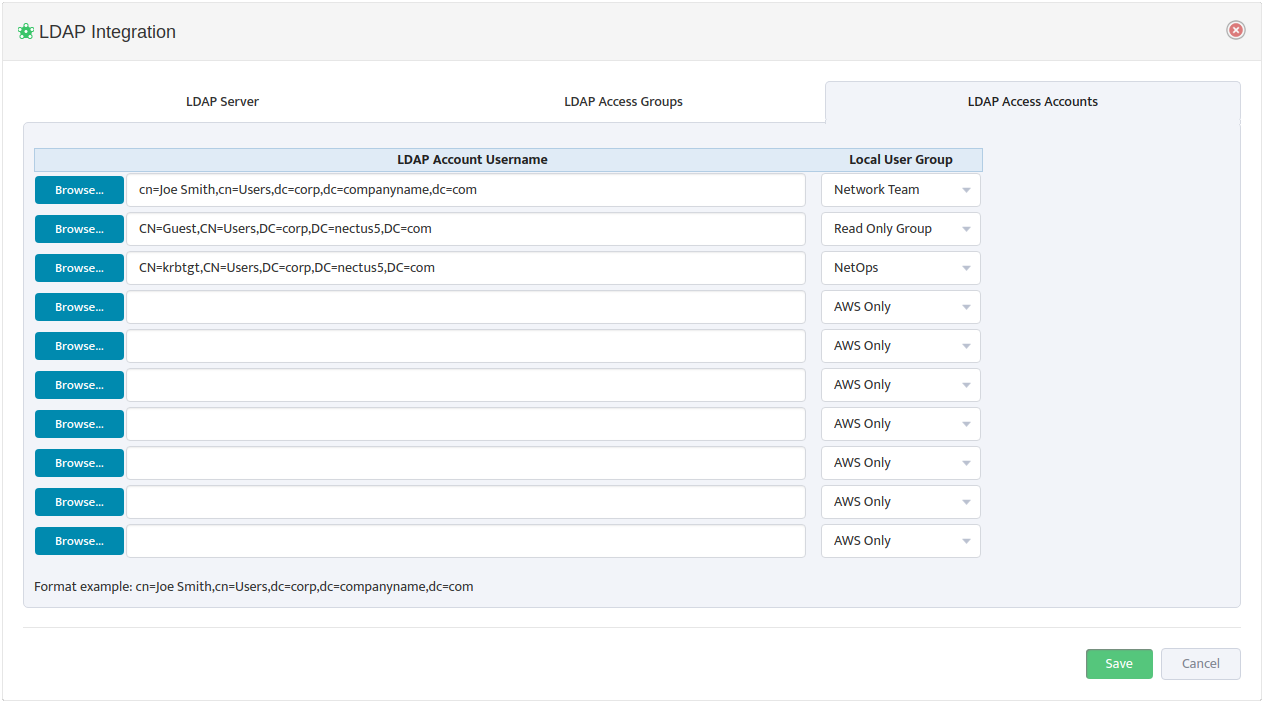
Use a Browse button on the left to open the “Select user from LDAP Server” dialog box and select an LDAP Account Username.
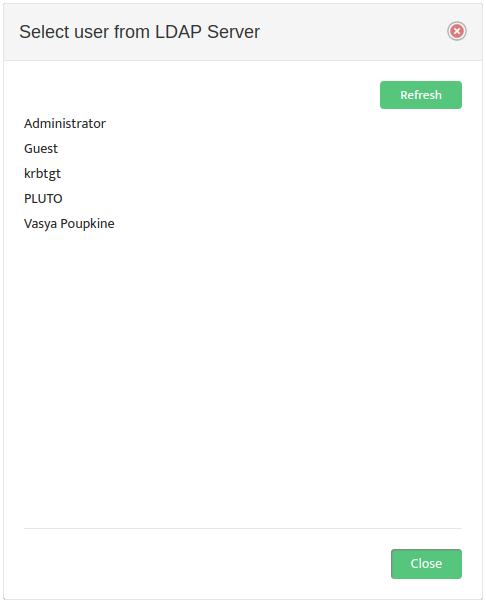
Nectus returns you to the “LDAP Integration” dialog box. In the drop-down list to the right, select the Local User Group to map the LDAP Account Username to. An example of the proper LDAP Account Username format appears at the bottom of the dialog box.
Monitoring Windows Server Storage Utilization with Nectus
Technical Notes, Windows Server (WMI) MonitoringMonitoring Windows Server Storage Utilization with Nectus
In this chapter, you’ll learn how to use WMI to monitor Windows Server Storage Utilization. Nectus lets you create Profiles that specify which Servers to monitor with WMI and to send Alerts related to them. It also provides graphs of Server Utilization over time.
The specific topics we will cover in this chapter are:
1. What is WMI?
WMI (Windows Management Instrumentation) is a set of specifications and interfaces that provides information about the status of local and remote computers running Microsoft Windows. In this chapter we look at how Nectus uses WMI to monitor the Storage Utilization on Windows Servers and send Alerts based on that information.
Note: WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM) standard and the Common Information Model (CIM) standard from the Distributed Management Task Force (DMTF).
2. Why Monitor Windows Server Storage Utilization?
Monitoring when Storage Utilization goes outside of the expected Thresholds alerts you to various problems. For example, exceeding the Maximum Threshold could indicate that a Server needs a larger disk, or that some other application is using space on the disk. Utilization below the Minimum Threshold could indicate that data is not being received by the Server, or a problem is keeping the data from being written to the disk.
3. Creating a WMI Server Group
To create a WMI Server Group open the WMI Servers Panel on the Nectus Home Screen. Right-click the WMI Servers list. In the menu that appears, click Add New Group.
This opens the “Add New WMI Server Group” dialog box.
Enter a Group Name, then select the Email Groups and SMS Groups that will receive Alerts.
4. Adding a Server to the WMI Server Group
To add a Windows Server to the WMI Server Group right-click the Group and select Add New WMI Server.
This opens the “Add WMI Server” dialog box.
Enter the IP address of the Server you want to add to the Group. Alternately, you can move a Server from its current Group to this Group by right-clicking the Server and using the Move WMI Server to option.
5. Creating and Configuring a WMI Monitoring Profile
To create a WMI Monitoring Profile go to the Nectus Home Screen and select Monitoring -> WMI Monitoring Settings.
This opens the “WMI Monitoring Settings” dialog box.
Click Add Profile -> Disk.
Enter the Monitoring Profile Name and check the Enabled box next to the Disk Used Space metric. Check the types of Alerts you want the Profile to send.
Check the Default Profile box if you want to make this the new default WMI Monitoring Profile.
5.1 Editing Disk Used Space Options
Select the Disk Used Space Options icon to open the “WMI Options – Disk Used Space, %” dialog box.
Set the Alert Thresholds you want to monitor, as well as the number of Consecutive Readings that a Threshold must be exceeded before triggering an alert. Nectus checks the thresholds every 5 minutes, so setting Consecutive Readings to 3 means a value would need to exceed the assigned Threshold for 15 minutes before triggering an alert.
5.2 Editing Disk Used Space Alert Templates
To edit the format of Alerts return to the Disk tab of the “Add WMI Monitoring Profile” dialog box. Click the Disk Used Space Alert Templates icon to open the “Edit Alert Handler” dialog box.
6. Assigning a Profile to the WMI Server Group
In the WMI Servers Panel on the Nectus Home screen, open the WMI Servers list. Right-click the WMI Server Group and select Properties.
This opens the “Edit WMI Server Group” dialog box.
Select the WMI Monitoring Profile to use from the Monitoring Profile drop-down list.
Check the Enable Monitoring box to begin monitoring the Server Group using this Monitoring Profile.
7. Viewing a Storage Utilization Graph
To view a graph of Storage Utilization over time, right-click the Server you want information on and select Disk Used Space Graph.
This opens a “Disk Used Space Graph” which displays the changes in Storage Utilization over time.
List of system variables that can be used in Alert emails for SNMP Devices and Interfaces
Network Monitoring, Technical NotesList of system variables that can be used in Alert emails for SNMP Devices and Interfaces (Version 2.48, January 2019).
More system variables will be added in next releases.
Device Hostname: %dev_hostname%
Device IPv4 Address: %dev_ipv4_address%
Device IPv6 Address: %dev_ipv6_address%
Device CPU Utilization: %dev_cpu_utilization%
Device RAM Utilization: %dev_ram_utilization%
Interface Name: %interface_name%
Interface Description: %interface_description%
Interface Rx Utilization: %interface_rx_utilization%
Interface Tx Utilization: %interface_tx_utilization%
Device Site: %dev_site_name%
Alert Time: %time%
Outage Duration: %outage_duration%
How to Configure Nectus Syslog Collector to use Local Storage
Syslog, Technical NotesHow to Configure Nectus Syslog Collector to use Local Storage
Settings → General Settings → Syslog Settings
“Syslog Remote Server DB Root Password” should be taken from this file:
C:\Program Files\Nectus\Web\Apache24\htdocs\protected\config\database.ini
“Settings → Services Status”
After Syslog Service is Restarted it should be ready to process and store Syslog Traffic.
How to Configure Nectus NetFlow Collector to use Local Storage
NetFlow IPFIX CFlow SFlow, Technical NotesHow to Configure Nectus NetFlow Collector to use Local Storage
To configure Nectus Netflow collector storage settings go to Main Menu
Settings → General Settings → NetFlow Integration
Configure Storage parameters according to this example:
“NetFlow Remote Server DB Root Password” should be taken from this file:
C:\Program Files\Nectus\Web\Apache24\htdocs\protected\config\database.ini
After Configuration is finished press “Test DB Connection” to test connectivity to DB
After DB connectivity is Tested, Press “Run Integration Scripts” button to create required SQL
Tables.
After Integration Scripts has been executed, Restart NetFlow collector service in
Top menu “Settings → Services Status”
After NetFlow Service is Restarted it should be ready to process NetFlow Traffic and store it in local DB.
Monitoring DHCP Scope Utilization on Windows DHCP Servers with Nectus
IPAM (IP Address Management), Technical Notes, Windows Server (WMI) MonitoringMonitoring Scope Utilization on Windows DHCP Servers with Nectus
In this chapter, you’ll learn how to use Nectus to enable and configure DHCP Scopes utilization monitoring on Windows DHCP Servers.
Nectus allows network engineers proactively monitor amount of free IP addresses in DHCP scopes and generate E-mail or Text alerts when number of free IP address falls below preset thresholds.
Nectus can also generate alert when number of free IP address exceeds predefined threshold as it may indicate underlying network operation problems when network devices not able reach DHCP server for leases.
Nectus uses basic WMI interface to collect scope and lease statistics from DHCP servers.
The specific topics we will cover in this chapter are:
1. What is WMI?
Nectus uses Windows Server WMI interface to collect basic information about DHCP scopes such as total number of IP addresses and current number of active leases.
WMI (Windows Management Instrumentation) is a set of specifications and interfaces that provides information about the status of local and remote computers running Microsoft Windows. In this chapter we look at how Nectus uses WMI to monitor DHCP Scope Utilization and send alerts based on that information.
Note: WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM) standard and the Common Information Model (CIM) standard from the Distributed Management Task Force (DMTF).
2. Why Monitor DHCP Scopes?
Availability of free IP addresses is a critical requirement for modern network. When DHCP scope runs out of addresses users are not able to join your network.
Typical network segments that heavily dependent on DHCP are LAN and Wi-Fi Users.
Several DDOS attack types are specifically targeting DHCP infrastructure and by exhausting DHCP pools with fake lease requests can bring down any network to its knees.
Sometimes regular business growth can cause corresponding grows in IP address utilization and if left undetected can eventual cause an outage and service degradation for DHCP dependent applications.
3. Creating a DHCP Server Group
First step is to create a new Server Group for our DHCP Servers.
Go to the Nectus Home Screen and select WMI Servers -> WMI Servers. In the menu that appears, click Add New Group.
This opens the “Add New WMI Server Group” dialog box.
Complete the fields that define the new Group and set Enable Monitoring.
4. Add a DHCP Server to Server Group
Now we need to define our DHCP Server and add those to Server Group.
To add a Windows DHCP Server to the Server Group right-click the Group and select Add New WMI Server.
This opens the “Add WMI Server” dialog box.
Enter the IP address of the Server you want to add to the Group.
Note: You can move a Server between different Groups by right-clicking the Server and using the Move WMI Server to option.
5. Creating and Configuring Monitoring Profile
Monitoring Profile is a list of Metrics that can be applied to Server Group to tell Nectus which specific metrics must be monitored for given Server Group.
To create new Monitoring Profile to go Monitoring -> WMI Monitoring Settings and press
“Add Profile” button
Monitoring Profile Configuration Interface will appear.
Assign Profile Name and enable “DHCP Scope Usage” check-button on “DHCP” Tab
Configure Max/Max Threshold Values for Alerts by pressing on “Options” button
Note: Monitoring Interval is 5 min therefore 3 for “Consecutive Readings” value will trigger Alert
only if Threshold condition are True for 15 minutes.
6. Assigning Monitoring Profile to Server Group
Next and the final step is to assign Monitoring Profile to the DHCP Server Group that we created.
Right Click on DHCP Server Group in left side panel and Select “Properties”
Select Monitoring Profile from the list of available Profiles and Click on “Enable Monitoring” check-button.
We are all set and ready to start proactive monitoring of your DHCP Infrastructure.
Download the best IPAM https://www.nectus5.com/download/
Importing subnets to IPAM from IGP routing protocols
IPAM (IP Address Management), Technical NotesImporting subnets to IPAM from IGP routing protocols
Most existing IPAM tools require manual subnet configuration, which is by far the most time-consuming step in IPAM deployment. Nectus offers unique automated features that make the initial configuration fast and easy. One such feature is an automatic import of subnets from the IGP routing protocols like OSPF, EIGRP, or ISIS. Here is how it’s done.
Importing subnets to IPAM from IGP
In the Main Menu, go to Inventory → IMAP Subnets and Reservations.
This opens an “IPAM Subnets” window with “IPv4 subnets” tab. Click the Import Subnets from Routing Table button.
In the “Import Subnet from IGP” dialogue box that appears, specify the IP address of the backbone router from which you’ll be importing subnets, and a destination IPAM container where the imported subnets will be placed. Press the Import button to preload the subnets.
Nectus displays preloaded subnets in a table format, for your confirmation. Press Yes button to confirm import of subnets, and they will automagically appear in the designated IPAM container.
Importing subnets to IPAM from DHCP servers
IPAM (IP Address Management), Technical NotesImporting subnets to IPAM from DHCP servers
One of the most time-consuming steps in IPAM deployment is initial configuration. Whether you have 5 or 1000 network subnets, most IPAM software products require manual configuration of subnets. Nectus offers unique automated features that make this initial configuration step fast and easy. One such feature is an automatic import of the subnets from the DHCP servers, which is done in 2 quick steps.
Adding DHCP servers to IPAM
Begin the process by configuring the DHCP servers on “IPAM integration” page. In the Main Menu, select Settings → General Settings → IPAM Integration.
This opens an “IPAM Integration” page. To add DHCP servers to IPAM, select the DHCP Servers tab and press the Add button to open the “Add DHCP Server” dialogue box. Fill in the server name, IP address and Type, and press the Save button for each DHCP server you want to add to IPAM.
Importing Subnets from DHCP Servers to IPAM
Once the DHCP servers are configured, you are now ready to start importing subnets. In the Main Menu, go to Inventory → IMAP Subnets and Reservations.
This opens an “IPAM Subnets” window with “IPv4 subnets” tab. Click the Import Subnets from DHCP Server button to open the “Import Subnet from DHCP Server” dialogue box.
Select the DHCP servers from which you’ll be importing subnets, and a destination IPAM container where the imported subnets will be placed. Press the Import button to preload the subnets.
Nectus displays preloaded subnets in a table format, for your confirmation. Press Yes button to confirm import of subnets, and they will automagically appear in your designated IPAM container.
Management Interface Selection for Network Devices
Network Discovery, Technical NotesManagement Interface Selection for Network Devices
In this chapter, you’ll learn how Nectus selects Management Interfaces for Devices that are found during Discovery phase. Nectus will automatically select Management Interfaces using its own default logic. It also supports user-defined selection for cases where this is appropriate.
The specific topics we will cover in this chapter are:
1. Default Logic for Management Interface Selection
During Discovery, Nectus finds all SNMP Devices on the network. Every Device has one or more Interfaces. Some of those Interfaces will have IP Addresses assigned to them, and could be used as the Management Interface for that Device.
Nectus has default logic for selecting the Management Interface for each Device. It checks every Interface on a Device looking for potential Management Interfaces. To be considered for selection as the Management Interface, an Interface must meet the following requirements:
From this list of possible Management Interfaces, Nectus selects one according to this priority list:
If Nectus finds an Interface name that begins with Mgmt, it will use this as the Management Interface. If it does not find an Interface name that begins with Mgmt, it will look for one that begins with Loopback, and so on.
If Nectus does not find an Interface whose name starts with Mgmt, Loopback, or Vlan, it will select the lowest numbered IP Address on the Device.
This default logic allows Nectus to automatically select the correct Management Interface in most situations. To handle situations where the default logic is not appropriate, Nectus supports user-defined logic for Management Interface selection.
2. User-Defined Logic for Management Interface Selection
Defining your own Management Interface selection logic makes sense in two situations:
When a Device has applicable user-defined Management Interface selection logic, Nectus looks for that Interface before applying the default logic. As with the default logic, user-defined Management Interfaces:
To create user-defined logic for a specific Device type right-click the Device name. In the menu that appears, select View Device Info.
This opens the “View Device Info” dialog box.
On the General Info tab, find the SNMP Platform ID and click the icon to the right of it to copy the ID.
Note: All Devices with the same model number have the same SNMP Platform ID.
Next Step is to go to Settings -> Products and Categories -> SNMP OID Libraries.
Select SNMP OID Libraries.
This opens the “SNMP OID Libraries” dialog box.
Select Management Interface Name in the Filter by OID Type list. Nectus displays all the current user-defined Management Interface Selection rules.
Click the Add button to open the “Add” dialog box.
Enter the SNMP Platform ID and the Management Interface Name Nectus should use for this type of Device.
3. Applying Selection Rules to Existing Devices
Defining new Management Interface selection rules will have automatic effect on all devices that will be discovered after rule is created but does not automatically apply those rules to existing Devices.
You need to tell Nectus to apply those changes to existing Devices.
To apply the user-defined selection rules to existing Devices, return to the “SNMP OID Libraries” dialog box and click the “Apply to Existing Devices” button.
Cisco SNMP v3 Configuration Example for IOS Devices
Network Discovery, Technical NotesThis is basic configuration example of the SNMPv3 on IOS device.
This enables SNMP v3 with following parameters:
Authentication Protocol: MD5
Authentication Username: vconsole
Authentication Password: nectus
Privacy (Encryption) Protocol: AES-256
Privacy (Encryption) Password: nectus
Configuration Example
====================
snmp-server group NECTUS_V3_GROUP v3 auth read TESTv3
snmp-server view TESTv3 mib-2 included
snmp-server user vconsole NECTUS_V3_GROUP v3 auth md5 nectus priv aes 256 nectus
Locating Orphaned subnets in IPAM
IPAM (IP Address Management), Technical NotesLocating Orphaned IPAM Subnets
One of the key features of good IPAM is ability quickly find subnets that are part of the defined address space but have not been explicitly added to list of subnets available for allocation.
These subnets are normally called “orphaned” and can be presented as white spaces within address space.
Orphaned subnets are normally occurring when you import IPAM subnets from external source such as IGP routing table where address space is not contiguously divided among all the existing subnets.
Lets looks at this simplified example of the logic required for locating orphaned subnets.
For example, user defined full address space as 10.0.0.0/8 (10.0.0.0 – 10.255.255.255)
and imported one subnet from IGP: 10.20.20.0/24 (10.20.20.0 – 10.20.20.255)
We can present full address space as a contiguous line starting from 10.0.0.0 and ending 10.255.255.255
Full IPv4 Address Space:
10.0.0.0 ———————————————————————————-10.255.255.255
Now let’s overlay single imported subnet into address space line:
10.0.0.0 ————-***Used*** —————————————————10.255.255.255
We see that there is some unused space to the left and to the right of the used space.
We need to find all the subnets that cover unused space so they can be presented in IPAM list of available subnets. The subnets that we are looking for must be largest subnets possible,
to minimize fragmentation.
Let’s summarize: Our goal is to find the largest subnet(s) that can be fit into the left and right empty segments.
Let first look at “left” empty space:
We can see that First and Last IP address of “left” empty segment have matching highest 11 bits.
Largest subnet that will fit into “left” empty segment will have First and Last IP with following parameters:
First IP address:
Last IP address:
After checking all possible options matching IP addresses are discovered.
This combination of First/Last IP gives us largest Subnet that will fit into “left” free segment as 10.0.0.0/12
We can see that 10.0.0.0/12 does not fully cover “left” empty segment so this discovery process has to be repeated for remaining empty space. Discovery may require several iterations until we get 100% coverage.
Similar approach must be applied to “right” empty segment until we identify all orphaned subnets and achieve 100% coverage of required address Space.
If your IPAM can’t perform this type of Discovery, you know where to download the best IPAM on the market: https://www.nectus5.com/download/
Splitting and Merging Subnets in IPAM
IPAM (IP Address Management), Technical NotesSplitting and Merging Subnets in IPAM
In this chapter, you’ll learn how and why to Split and Merge Subnets.
The specific topics we will cover in this chapter are:
1. Why Split or Merge Subnets?
Splitting and Merging Subnets lets you use your IP address space more efficiently. A full Class C Subnet has 256 usable addresses. But if you only need 30, using the full Subnet would result in a waste of over 200 IP addresses. Splitting the subnet would allow you to get the number of addresses you need, without wasting the rest. In addition, making a smaller Subnet reduces network traffic, as messages on that Subset are broadcast to fewer addresses.
Merging Subnets works the opposite. You may need a Subnet with 80 IP addresses, but instead have several smaller Subnets available. By merging smaller Subnets into one large one, you can use those addresses that might otherwise be wasted.
Nectus also allows you to move Subnets to different IPAM Containers. This makes it easy to reallocate IP addresses from their current location to the physical Sites that need them.
2. How to Split Subnets
To Split a Subnet go to the Nectus Sites Panel and select IPAM > All IPv4 Containers.
Nectus displays all existing IPAM Containers and any Unassigned Subnets. To see how many IP addresses are available in any Subnet, right-click it. In the menu that appears, select View Subnet Info.
This opens the “Subnet View Info” dialog box.
The Total IPs field on the General Info tab shows how many IPs the Subnet contains.
Navigate to the Subnet you want to split and right-click it. In the menu that appears, select Split.
This opens the “Split Subnet” dialog box.
The New Subnet Size list shows you the ways you can split the selected Subnet.
The Place New Subnets to: list allows you to assign the new Subnets you create to any existing IPAM Container.
3. How to Merge and Subnets
To Merge two or more Subnets go to the Nectus Sites Panel and select IPAM > All IPv4 Containers.
Navigate to the Subnets you want to merge and select each one. The Subnets you want to Merge must be contiguous, as in the screenshot below. Right-click one of the Subnets and in the menu that appears, select Merge Subnets.
This opens the “Merge Subnets” dialog box. The dialog box shows you which Subnets will be merged, and gives you the option to place the merged Subnet in any IPAM Container.
4. How to Move Subnets
You can move a Subnet without Splitting or Merging it. To move a Subnet to a different IPAM Container right-click the Subnet.
In the menu that appears, select Move Subnet to… and navigate the list of Containers to select the new location.
IPAM initial configuration automation: Subnets
IPAM (IP Address Management), Technical NotesIPAM initial configuration automation: Subnets
As soon as you install your favorite Nectus IPAM solution the first question that comes to your mind is “How do I add all of the existing Subnets into new IPAM”?
Let’s see what automation options does Nectus offer to ease your initial deployment pains.
There are three primary places where your existing subnets can be imported from
Importing from IGP
Importing most of your subnets from IGP is the primary way to get most (if not all) of your subnets into IPAM in a single click of the button. Just right click on IPAM container Tree and select “Import Subnets from Routing Table” Option.
Provide your Core Router’s IP Address and press “Import” button
Nectus will download IGP routing table from core router via SNMP and add each subnet into IPAM database. When importing subnets from IGP Nectus starts loading subnets starting from
smallest (/32) to biggest (/8 and higher). Each new added subnet is validated against overlapping with any of the existing IPAM subnets.
This logic ensures that summarized prefixes that are present in the routing table will not be added to IPAM.
Nectus does not import any BGP subnets to prevent public Internet prefixes leaking into IPAM.
You can repeat IGP Import several times with different Core routers if there is a reason to believe that different Core routers may produce different set of subnets.
Importing from DHCP Servers
Importing subnets from DHCP Servers works similarly to IGP Import. Right Click on any of the IPAM containers and Select “Import Subnets from DHCP” Option.
Nectus load all the DHCP pools from all the DHCP servers configured in “IPAM Integration” page and add those into IPAM database if they have not been already added during IGP Import Phase.
All the subnets imported from DHCP Servers are validated against overlapping with any of the existing IPAM subnets.
Currently DHCP Import is only supported for Microsoft Windows DHCP servers and require
operational WMI Integration configuration.
Importing from CSV Files
And final and still viable option is to Import your subnets from CSV File.
Select “Import from CSV” in context menu of any of the IPAM Containers to load your subnets from CSV File.
Finding Unused Subnets
Once you finished loading your “in-use” Subnets into IPAM next step is to identify what subnets are “available” since subnets that are not allocated yet will not be present in the IGP or DHCP Servers.
To identify unused subnets Nectus takes your Address Space Subnets defined in IPAM Global integration page and excludes all of the “in-use” subnets to calculate list of subnets that can be presented as available. All available subnets will be added to “Unassigned Subnets” default IPAM container.
Right-click on any IPAM container to access this menu option.
Making IP Reservations in Nectus IPAM
IPAM (IP Address Management), Technical NotesMaking IP Reservations in Nectus IPAM
In this chapter, you’ll learn how to make IP reservations in Nectus IPAM.
The specific topics we will cover in this chapter are:
1. Adding New IP Reservation
To create a new IP Reservation, navigate to desired Subnet in selected IPAM container
and right-click for context menu.
Click on “Reservations” option to bring up a list of current Reservations in this specific Subnet.
Switch to a “MAP” Tab to see what is available for Reservations in this subnet
Righ- Click on Selected IP on the MAP and Select “Add IPv4 To Reservation”
Fill all the desired reservation parameters and press “ADD” button
As part of IP reservation creation process you have an option to create DNS “A” Records
in forward and reverse DNS lookup zones with DNS Server configured on IPAM Integration Page.
2. How to Delete IP Reservation
To delete IP reservation right click on desired reservation on subnet MAP view Page and select “Delete Reservation” Option
As part of reservation deletion process, you can also automatically delete DNS “A” records on DNS servers if those records were previously added during reservation creation process.
3. Searching for IPAM Reservation
Best way to search for existing IP reservations is via “IPAM Subnets and Reservations” Table
located in “Inventory -> IPAM Subnets and Reservations” Page
Table view provides multiple search and filtering options for any parameters defined for IP reservations.
Managing IPAM Containers in Nectus
IPAM (IP Address Management), Technical NotesManaging IPAM Containers in Nectus
In this chapter, you’ll learn what IPAM Containers are and how to manage them.
The specific topics we will cover in this chapter are:
1. What are IPAM and IPAM Containers?
IPAM stands for Internet Protocol Address Management. It is a system for managing the Internet Protocol (IP) address space used in a network. With IPAM you can see which IP subnets are in use and which site is using them.
The Nectus IPAM Container model allows you to create a hierarchical structure for managing subnets and mapping them to physical Sites.
2. How to Create IPAM Containers
To create an IPv4 IPAM Container go to the Nectus IPAM Panel and select IPAM -> All IPv4 Containers.
Nectus displays any existing IPAM Containers. Containers that have subnets assigned to them are displayed in green, with the number of subnets they contain appearing to the right of the Container name.
To add a new IPAM Container right-click an existing Container or All IPv4 Containers. In the menu that appears select Create New Container Level.
This opens the “Create New Container Level” dialog box.
Enter the Container Level Name and click Save. The new Container appears in the hierarchy below the location shown in Container Path:.
3. How to Move IPAM Containers
To move an IPAM Container right-click the Container Name. In the menu that appears, select Move Current Container to… and navigate the list of Containers to select the new location.
4. How to Modify IPAM Containers
To modify an IPAM Container right-click the Container Name. In the menu that appears, select Properties.
This opens the “Edit Container Properties” dialog box.
Edit the Container Level Name as desired.
5. How to Delete IPAM Containers
To modify an IPAM Container right-click the Container Name. In the menu that appears, select Delete Current Container Level.
This opens the “Delete Container Level” dialog box.
Note: Nectus will not let you delete an IPAM Container that has subnets assigned to it. If you try, Nectus displays the following message:
Configuring AD LDAP Integration for User Authentication
Access Right Management, Technical NotesConfiguring AD/LDAP Integration for User Authentication
In this chapter, you’ll learn how to configure Nectus to work with Microsoft Active Directory and the LDAP protocol for user authentication.
The specific topics we will cover in this chapter are:
1. What are AD and LDAP?
AD stands for Active Directory Domain Services. It is a Microsoft service that provides authentication and other services to devices on a network. It is an LDAP compliant database of users, groups, and other objects.
LDAP stands for Lightweight Directory Access Protocol. It is an Internet standard for accessing distributed directory services. Nectus uses LDAP to communicate with AD.
2. Why Configure Nectus Integration with AD/LDAP?
Configuring Nectus to integrate with AD/LDAP simplifies user management for large organizations. Like most applications, Nectus has its own local user authentication database. But when a organization has many applications maintaining separate user accounts for each application isn’t practical.
The solution is to maintain user accounts in AD. Using LDAP, each application can query the AD database for the user authentication information it needs. This greatly simplifies user account maintenance.
3. How Nectus Authenticates Users
Nectus is designed to function on its own or integrated with AD/LDAP. Security settings are based on Local User Groups whether the User Account is stored locally, or in AD.
When a user logs in Nectus first checks to see if the active user has a Local User Account. If so, Nectus uses this account for the login.
Note: To manage the Nectus Local User Accounts and the Local User Groups go to the Nectus Home Screen and select Settings -> Admin Accounts. This opens the “Admin Accounts” dialog box. See the article, “Creating User Accounts and User Groups” for details.
If the active user does not have a Local User Account, Nectus checks to see if Active Directory integration is configured. If so, it checks to see if the active user has an account in AD.
If the user has an account in AD, and the user’s LDAP Group Name is mapped to a Local User Group, Nectus uses the Local User Group settings.
If there is no mapping to a Local User Group, Nectus checks to see if the active user’s LDAP Account Username is mapped to a Local User Group and uses those settings.
If none of the above is true, Nectus denies the user access.
Important: We recommend that you always maintain at least one Local User Account in Nectus to ensure access even if the AD/LDAP connection is down.
4. Connecting Nectus to an LDAP Server
To integrate Nectus with AD you need to configure the LDAP Server settings and enable LDAP.
To configure the LDAP Server settings and enable LDAP go to the Nectus Home Screen and select Settings -> LDAP Integration.
This opens the “LDAP Integration” dialog box.
Select the LDAP Server tab and enter the LDAP parameters. You can see examples of the format for these parameters to the right of the relevant fields. Check LDAP Enabled.
5. Mapping AD/LDAP Groups to Nectus Local User Groups
Mapping an AD/LDAP Group to a Nectus Local User Group causes the entire AD/LDAP group to inherit the security settings from the Nectus Local User Group.
To map AD/LDAP Groups to Nectus Local User Groups, open the “LDAP Integration” dialog box and select the LDAP Access Groups tab.
Use a Browse button on the left to open the “Select group from LDAP Server” dialog box and select an LDAP Group Name.
Nectus returns you to the “LDAP Integration” dialog box. In the drop-down list to the right of the LDAP Group Name, select the Local User Group to map it to. An example of the proper LDAP Group Name format appears at the bottom of the dialog box.
6. Mapping AD/LDAP Usernames to Nectus Local User Groups
Mapping an AD/LDAP Username to a Nectus Local User Group causes the specific AD/LDAP User to inherit the security settings from the Nectus Local User Group.
To map AD/LDAP Account Usernames to Nectus Local User Groups, open the “LDAP Integration” dialog box and select the LDAP Access Accounts tab.
Use a Browse button on the left to open the “Select user from LDAP Server” dialog box and select an LDAP Account Username.
Nectus returns you to the “LDAP Integration” dialog box. In the drop-down list to the right, select the Local User Group to map the LDAP Account Username to. An example of the proper LDAP Account Username format appears at the bottom of the dialog box.
Preventing Specific Subnets from Being Discovered by Nectus
Network Discovery, Technical NotesPreventing Specific Subnets from Being Discovered by Nectus
In this chapter, you’ll learn how to prevent specific subnets from being discovered by Nectus.
The specific topics we will cover in this chapter are:
1. Why Prevent Specific Subnets from Being Discovered?
Preventing specific IP subnets from being discovered can provide improved security. For example, if your client is a city government, they might want to hide the Subnet of the police force or other crucial services. A bank might want to hide the Subnet that their ATMs run on.
2. How Does Nectus Prevent Specific Subnets from Being Discovered?
Before Nectus scans the network, it consults the Excluded Subnets List. It doesn’t scan any Subnets it finds in this list and deletes any information about those Subnets from the Management Information Base (MIB).
3. Working with the Excluded Subnet List
To work with the Excluded Subnet List go to the Nectus Home Screen and select Settings -> Network Discovery Settings.
This opens the “WMI Monitoring Settings” dialog box. Select the Excluded Subnets tab.
Click Add to open the “Add Excluded Subnet” dialog box.
Enter the IPv4 Subnet and the number of Mask bits to identify the Subnet you want excluded.
Note: If you remove a Subnet from the Excluded Subnet List, it, and all the Devices on it, will appear the next time Nectus runs Discovery.
Preventing Specific Devices from Being Discovered by Nectus
Network Discovery, Technical NotesPreventing Specific Devices from Being Discovered by Nectus
In this chapter, you’ll learn how to prevent specific Device types from being discovered by Nectus.
The specific topics we will cover in this chapter are:
1. Why Prevent Specific Devices from Being Discovered?
Preventing certain Device types from being discovered and displayed in the SNMP Devices list makes it easier to manage your network device inventory.
For example, you could have hundreds of printers connected to your network. But under normal circumstances, you probably don’t need to monitor them.
Preventing Nectus from discovering specific devices saves Nectus Server resources for the devices you really want to monitor.
2. How Does Nectus Prevent Specific Devices from Being Discovered?
During discovery Nectus collects information about every network device it finds. This information include SNMP Platform OID.
Nectus maintain “SNMP Platform OID Ignore-List” which contains a list of SNMP Platform IDs that should be ignored during discovery.
By adding specific SNMP Platform OID to “Ignore-List” you can prevent devices with that Platform ID from being added by Nectus to its database.
3. Adding Devices to the Ignore OID List
To add a Device type to the Ignore OID List, go to the “SNMP Devices” Panel on the Nectus Home screen and open the All Devices list. Navigate to the Product Specific Level containing the type of Device you want to hide and right-click on it. In the shortcut menu that appears, select Add to Ignore List and Delete.
Confirm the operation in the “Add to Ignore List and Delete” dialog box that appears.
Nectus adds the Device type to the Ignore OID List and removes this Sub-Category and all its Devices from the SNMP Devices list.
4. Editing the Ignore OID List
You can manually edit the Ignore OID List to hide Device types, make them discoverable again, or change the OID Prefix associated with them.
To edit the Ignore OID List go to the Nectus Home Screen and select Settings -> Network Discovery Settings.
This opens the “WMI Monitoring Settings” dialog box. Select the Ignore OID List tab.
Use the controls here to add Device types to the Ignore OID List or remove them from it. Any previously hidden Devices will appear the next time Discovery runs.
You can also manually change the OID Prefix by clicking the Edit icon to the right of the Sub-category to open the “Update OID” dialog box.
Monitoring Windows Event Log with WMI in Nectus
Technical Notes, Windows Server (WMI) MonitoringMonitoring Windows Event Log with WMI
In this chapter, you’ll learn how to use WMI to monitor the Windows Event Log. Nectus lets you create profiles that use WMI to monitor specific Events and to send Alerts related to them.
The specific topics we will cover in this chapter are:
1. What is WMI?
WMI (Windows Management Instrumentation) is a set of specifications and interfaces that provides information about the status of local and remote computers running Microsoft Windows. In this chapter we look at how Nectus uses WMI to monitor the status of Windows Processes and send Alerts based on that status.
Note: WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM) standard and the Common Information Model (CIM) standard from the Distributed Management Task Force (DMTF).
2. Why Monitor the Windows Event Log?
There are many reasons to monitor the Windows Event Log. One of the most important is preventing security breaches. Events that show a configuration change, a failure, or an unexpected login attempt could be triggered by an attack on the server.
3. Creating a WMI Monitoring Profile
To create a WMI Monitoring Profile go to the Nectus Home Screen and select Monitoring -> WMI Monitoring Settings.
This opens the “WMI Monitoring Settings” dialog box.
Click Add Profile -> System.
Create a new Profile by entering the Monitoring Profile Name and checking the Event log monitoring Enabled box. In addition, check the types of Alerts you want to send. See Section 4, “Editing a WMI Monitoring Profile” for details on how to specify which Events you want to monitor and how you want to be alerted.
Check the Default Profile box if you want to make this the new default WMI Monitoring profile.
4. Configuring Event Log Monitoring
To configure Event Log monitoring, open the “WMI Monitoring Settings” dialog box and select the Edit Profile icon for the Profile you want to edit. In “Edit WMI Monitoring Profile” dialog box that appears select the System tab.
4.1 Editing Options
Select the Event log monitoring Options icon to open the “WMI Event Log Filters” dialog box.
Click Add Filter to open the “Add Event Log Filter” dialog box.
Enter the Filter Name and optionally select a specific Event Log File to monitor. Fill out the rest of the fields as necessary to specify the Event you want to monitor. The new filter will appear in the “WMI Event Log Filters” dialog box.
4.2 Editing Alerts and Templates
In the System tab of the “Edit WMI Monitoring Profile” dialog box, check or clear the types of Alerts to send for the Events. To edit the format of the Alerts, open the “Edit Alert Handler” dialog box by clicking the Edit Alert Templates icon.
5. Assigning a Profile to a WMI Server Group
In the WMI Servers Panel on the Nectus Home screen, open the WMI Servers list. Right-click a WMI Server Group and select Properties.
This opens the “Edit WMI Server Group” dialog box.
Check the Enable Monitoring box, then select the WMI Monitoring Profile to use from the Monitoring Profile drop-down list, and specify which groups will receive the Alerts.
The icons to the right of the Monitoring Profile list allow you to edit a Profile or add a new Profile directly from here.
Monitoring Windows Processes with WMI in Nectus
Technical Notes, Windows Server (WMI) MonitoringMonitoring Windows Processes with WMI
In this chapter, you’ll learn how to use WMI to monitor Windows Processes. Nectus lets you create profiles that specify which Processes to monitor with WMI and to send Alerts related to them.
The specific topics we will cover in this chapter are:
1. What is WMI?
WMI (Windows Management Instrumentation) is a set of specifications and interfaces that provides information about the status of local and remote computers running Microsoft Windows. In this chapter we look at how Nectus uses WMI to monitor the status of Windows Processes and send Alerts based on that status.
Note: WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM) standard and the Common Information Model (CIM) standard from the Distributed Management Task Force (DMTF).
2. Why Monitor Windows Processes?
You will normally want a particular set of Windows Processes running on your servers. Nectus can notify you when these Processes run, ensuring you that everything starts properly. You can also watch for specific Processes you don’t want on your servers.
For example, viruses run as Processes. If you know the names of the Processes associated with a specific virus, Nectus can notify you if any of those Processes starts running on one of your servers.
Monitoring for stopped Windows Processes lets you respond quickly to the failure of an important business Process.
3. Creating a WMI Monitoring Profile
To create a WMI Monitoring Profile go to the Nectus Home Screen and select Monitoring -> WMI Monitoring Settings.
This opens the “WMI Monitoring Settings” dialog box.
Click Add Profile -> Processes.
Create a new Profile by entering the Monitoring Profile Name and checking the Enabled boxes next to the metrics you want to monitor. In addition, check the types of Alerts you want to send for each Monitored Metric. See Section 4, “Editing a WMI Monitoring Profile” for details on how to specify which Processes you want to monitor and how you want to be alerted.
Check the Default Profile box if you want to make this the new default WMI Monitoring profile.
4. Editing a WMI Monitoring Profile
To edit a WMI Monitoring Profile, open the “WMI Monitoring Settings” dialog box and select the Edit Profile icon for the Profile you want to edit. In “Edit WMI Monitoring Profile” dialog box that appears select the Processes tab.
4.1 Editing Options
Select the Options icon for the Metric you want to edit to open the “WMI Options” dialog box.
Set the number of Consecutive Readings needed to trigger an alert then click the Add Name button to add the Processes you want to monitor.
4.2 Editing Alerts and Templates
In the Processes tab of the “Edit WMI Monitoring Profile” dialog box, check or clear the types of Alerts to send for each Monitored Metric. To edit the format of the Alerts, open the “Edit Alert Handler” dialog box by clicking the Edit Alert Templates icon.
5. Assigning a Profile to a WMI Server Group
In the WMI Servers Panel on the Nectus Home screen, open the WMI Servers list. Right-click a WMI Server Group and select Properties.
This opens the “Edit WMI Server Group” dialog box.
Check the Enable Monitoring box, then select the WMI Monitoring Profile to use from the Monitoring Profile drop-down list, and specify which groups will receive the Alerts.
The icons to the right of the Monitoring Profile list allow you to edit a Profile or add a new Profile directly from here.
Monitoring of Windows Services with WMI in Nectus
Windows Server (WMI) MonitoringMonitoring of Windows Services with WMI in Nectus
In this chapter, you’ll learn how to use WMI to monitor Windows Services. Nectus lets you create profiles that specify which services to monitor with WMI and how to send alerts related to them.
The specific topics we will cover in this chapter are:
1. What is WMI?
WMI (Windows Management Instrumentation) is a set of specifications and interfaces that provides information about the status of local and remote computers running Microsoft Windows. In this chapter we look at how Nectus uses WMI to monitor the status of Windows Services and send Alerts based on that status.
Note: WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM) standard and the Common Information Model (CIM) standard from the Distributed Management Task Force (DMTF).
2. Why Monitor Windows Services?
Knowing which Windows Services are running lets you spot misconfigured servers easily. You can ensure that all required services such as anti-virus software are running. You can also see if any unwanted services such as a web server are running.
Monitoring for stopped Windows Services lets you respond to the failure of an important service quickly.
3. Creating a WMI Monitoring Profile
To create a WMI Monitoring Profile go to the Nectus Home Screen and select Monitoring -> WMI Monitoring Settings.
This opens the “WMI Monitoring Settings” dialog box.
Click Add Profile -> Services.
Create a new Profile by entering the Monitoring Profile Name and checking the Enabled boxes next to the metrics you want to monitor. In addition, check the types of Alerts you want to receive for each Monitored Metric. See Section 4, “Editing a WMI Monitoring Profile” for details on how to specify which Services you want to monitor and how you want to be alerted.
Check the Default Profile box if you want to make this the new default WMI Monitoring profile.
4. Editing a WMI Monitoring Profile
To edit a WMI Monitoring Profile, open the “WMI Monitoring Settings” dialog box and select the Edit Profile icon for the Profile you want to edit. In “Edit WMI Profile” dialog box that appears select the Services tab.
4.1 Editing Options
Select the Options icon for the Metric you want to edit to open the “WMI Options” dialog box.
Set the number of Consecutive Readings needed to trigger an alert then click the Add Name button to add the Services you want to monitor.
4.2 Editing Alerts and Templates
In the Services tab of the “Edit WMI Monitoring Profile” dialog box, check or clear the types of Alerts to receive for each Monitored Metric. To edit the format of the Alerts, open the “Edit Alert Handler” dialog box by clicking the Edit Alert Templates icon.
5. Assigning a Profile to a WMI Server Group
In the WMI Servers Panel on the Nectus Home screen, open the WMI Servers list. Right-click a WMI Server Group and select Properties.
This opens the “Edit WMI Server Group” dialog box.
Check the Enable Monitoring box, then select the WMI Monitoring Profile to use from the Monitoring Profile drop-down list, and specify which groups will receive the Alerts.
The icons to the right of the Monitoring Profile list allow you to edit a Profile or add a new Profile directly from here.