Configuring AD/LDAP Integration for User Authentication
In this chapter, you’ll learn how to configure Nectus to work with Microsoft Active Directory and the LDAP protocol for user authentication.
The specific topics we will cover in this chapter are:
- What are AD and LDAP?
- Why Configure Nectus Integration with AD/LDAP?
- How Nectus Authenticates Users
- Connecting Nectus to an LDAP Server
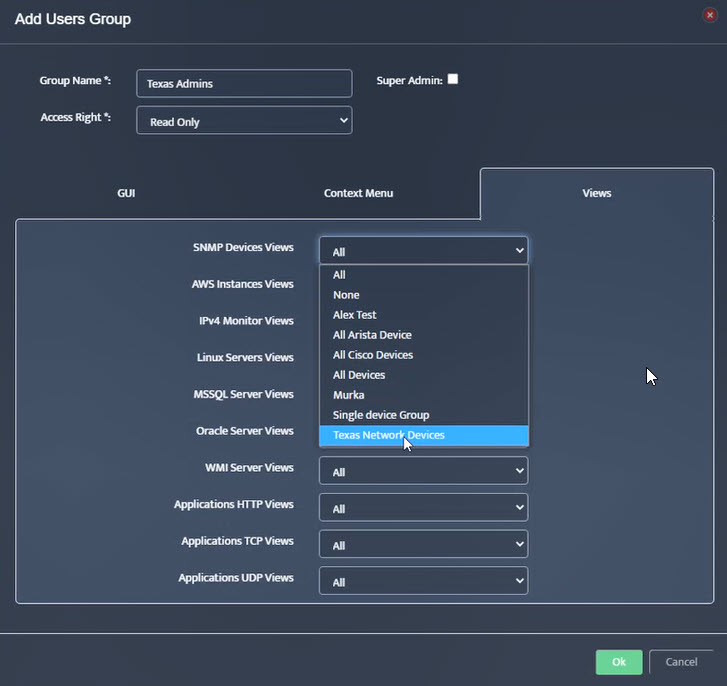
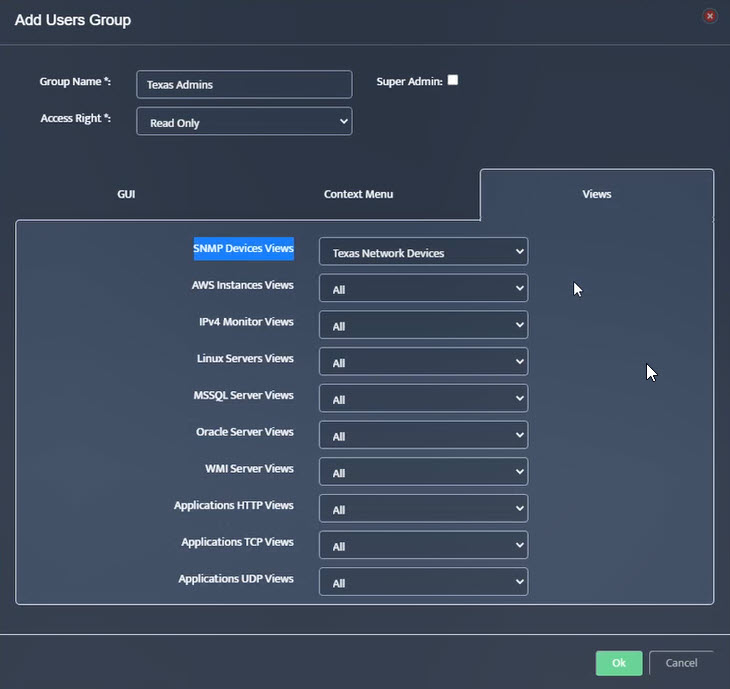
- Mapping AD/LDAP Groups to Local User Groups
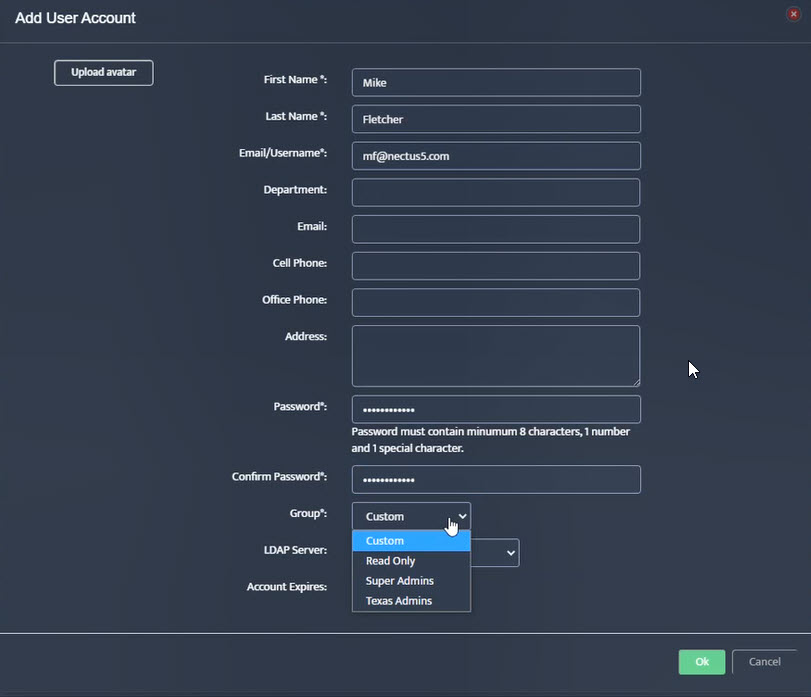
- Mapping AD/LDAP Users to Local User Groups
1. What are AD and LDAP?
AD stands for Active Directory Domain Services. It is a Microsoft service that provides authentication and other services to devices on a network. It is an LDAP compliant database of users, groups, and other objects.
LDAP stands for Lightweight Directory Access Protocol. It is an Internet standard for accessing distributed directory services. Nectus uses LDAP to communicate with AD.
2. Why Configure Nectus Integration with AD/LDAP?
Configuring Nectus to integrate with AD/LDAP simplifies user management for large organizations. Like most applications, Nectus has its own local user authentication database. But when a organization has many applications maintaining separate user accounts for each application isn’t practical.
The solution is to maintain user accounts in AD. Using LDAP, each application can query the AD database for the user authentication information it needs. This greatly simplifies user account maintenance.
3. How Nectus Authenticates Users
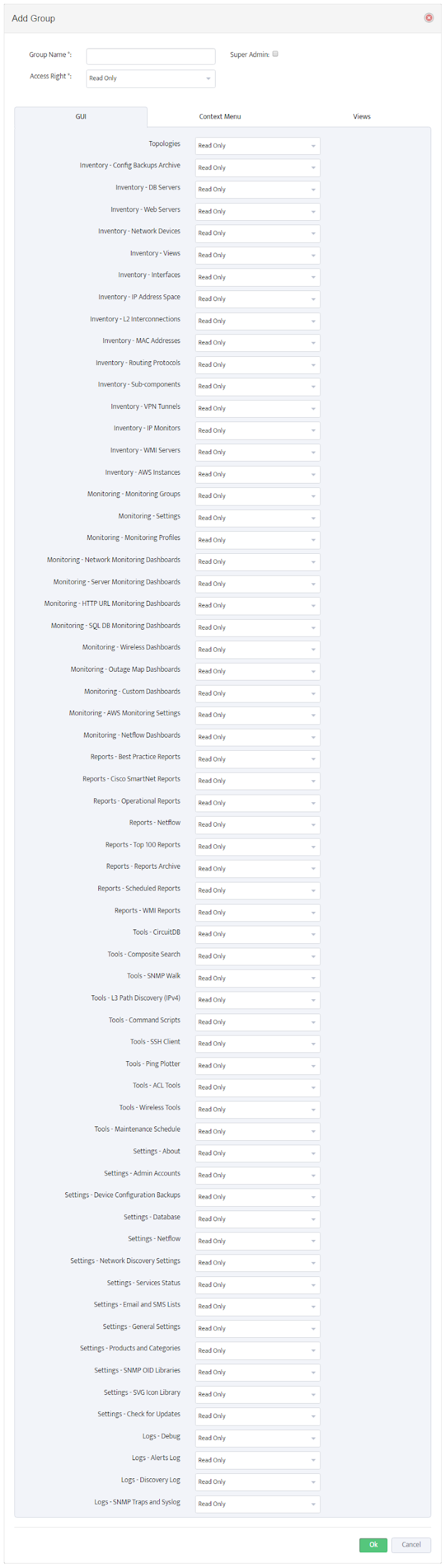
Nectus is designed to function on its own or integrated with AD/LDAP. Security settings are based on Local User Groups whether the User Account is stored locally, or in AD.
When a user logs in Nectus first checks to see if the active user has a Local User Account. If so, Nectus uses this account for the login.
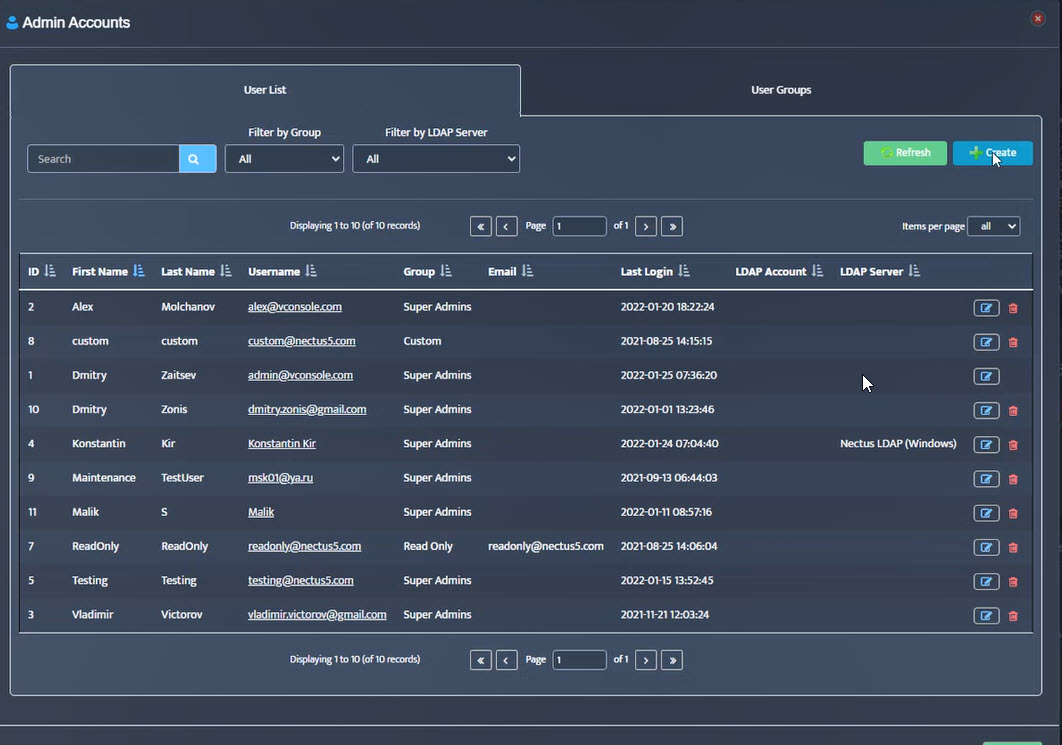
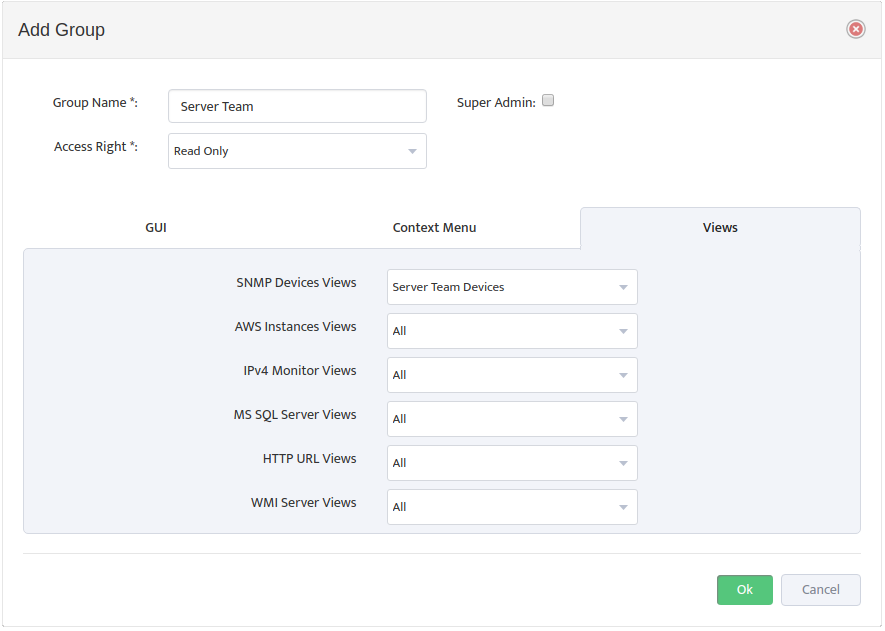
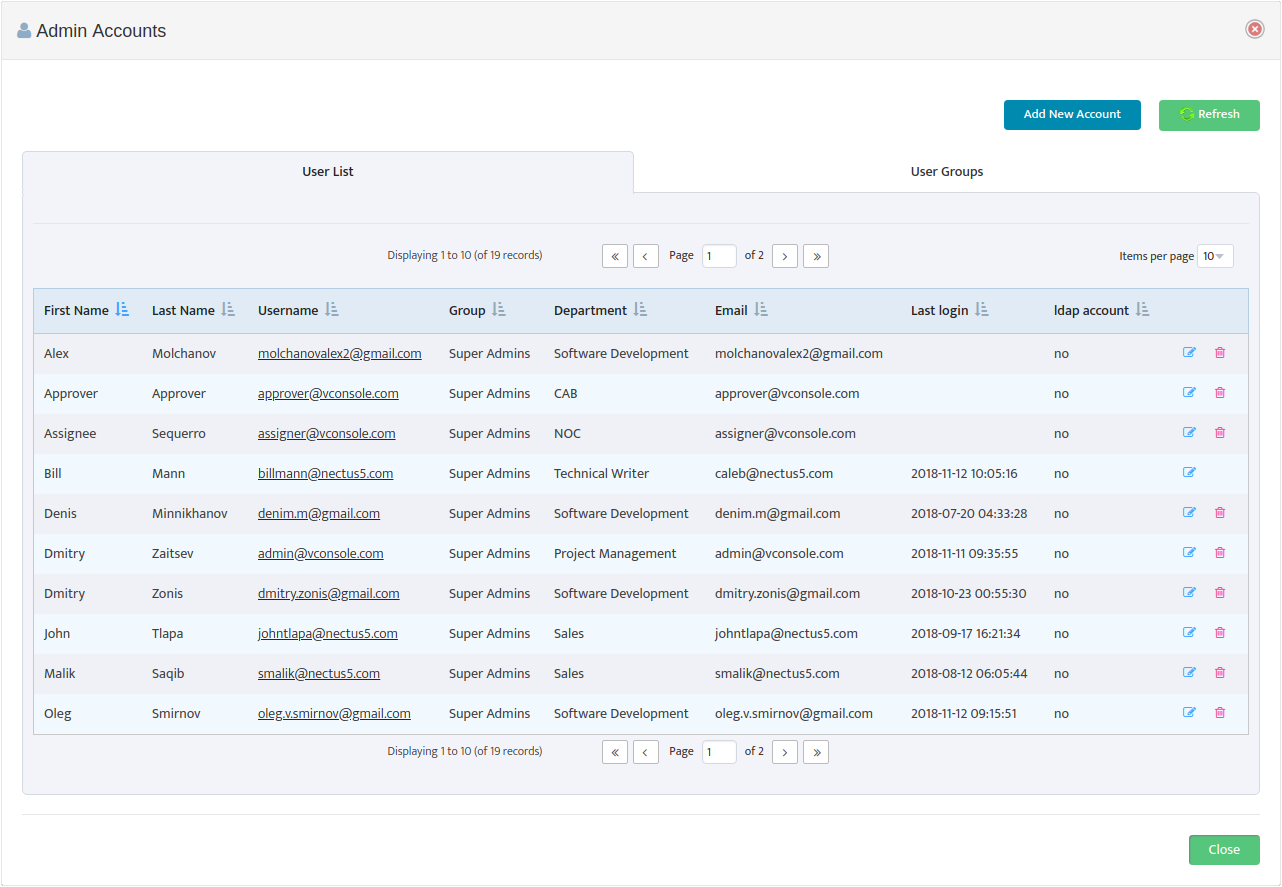
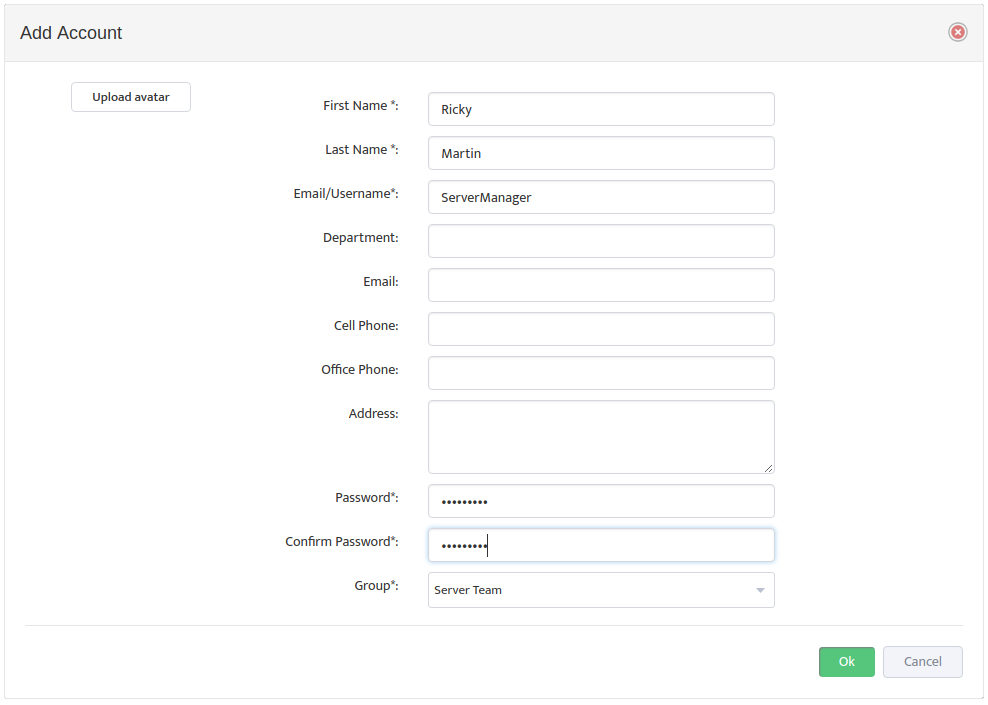
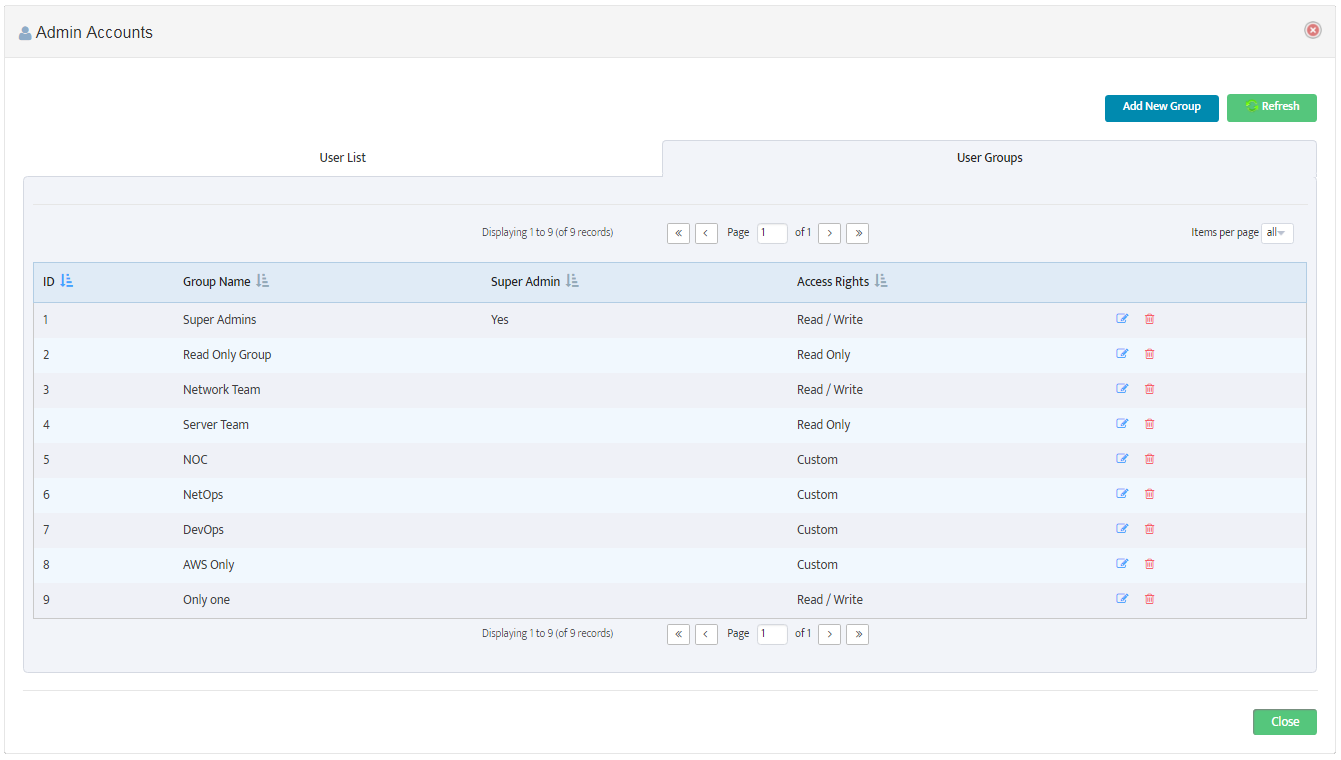
Note: To manage the Nectus Local User Accounts and the Local User Groups go to the Nectus Home Screen and select Settings -> Admin Accounts. This opens the “Admin Accounts” dialog box. See the article, “Creating User Accounts and User Groups” for details.
If the active user does not have a Local User Account, Nectus checks to see if Active Directory integration is configured. If so, it checks to see if the active user has an account in AD.
If the user has an account in AD, and the user’s LDAP Group Name is mapped to a Local User Group, Nectus uses the Local User Group settings.
If there is no mapping to a Local User Group, Nectus checks to see if the active user’s LDAP Account Username is mapped to a Local User Group and uses those settings.
If none of the above is true, Nectus denies the user access.
Important: We recommend that you always maintain at least one Local User Account in Nectus to ensure access even if the AD/LDAP connection is down.
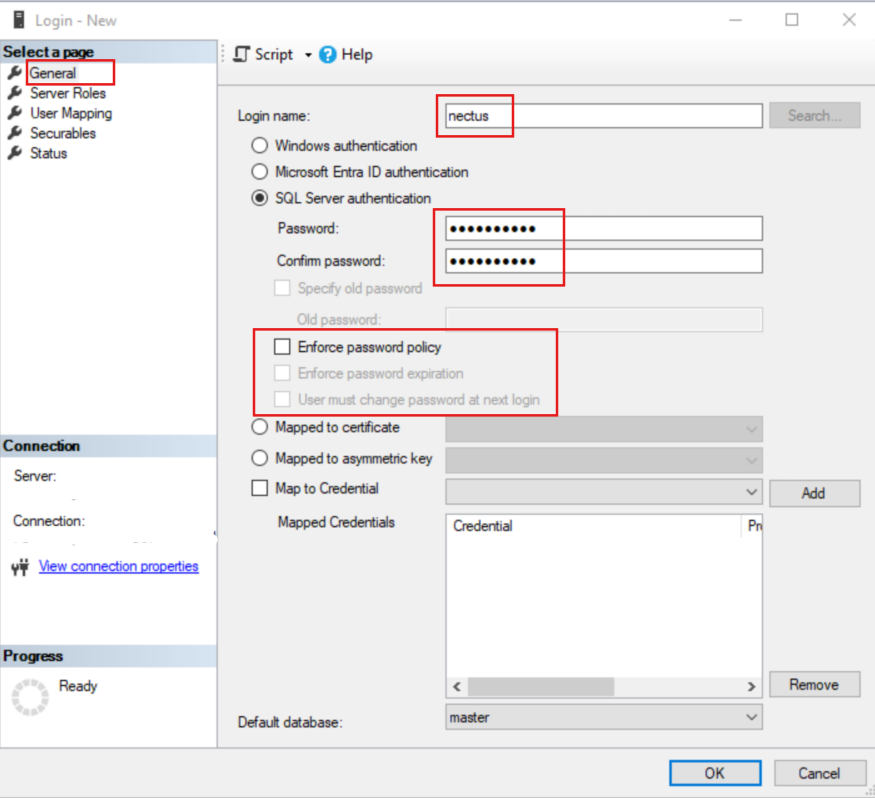
4. Connecting Nectus to an LDAP Server
To integrate Nectus with AD you need to configure the LDAP Server settings and enable LDAP.
To configure the LDAP Server settings and enable LDAP go to the Nectus Home Screen and select Settings -> LDAP Integration.
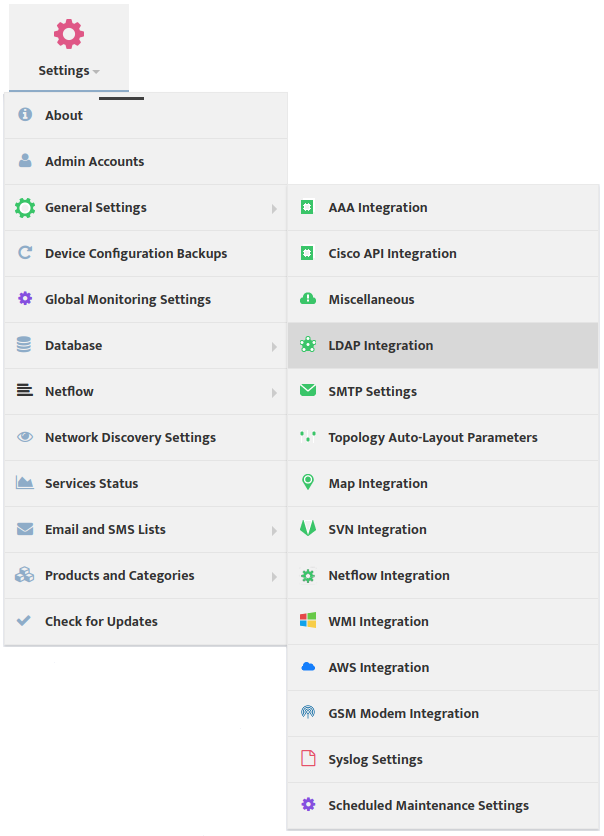
This opens the “LDAP Integration” dialog box.
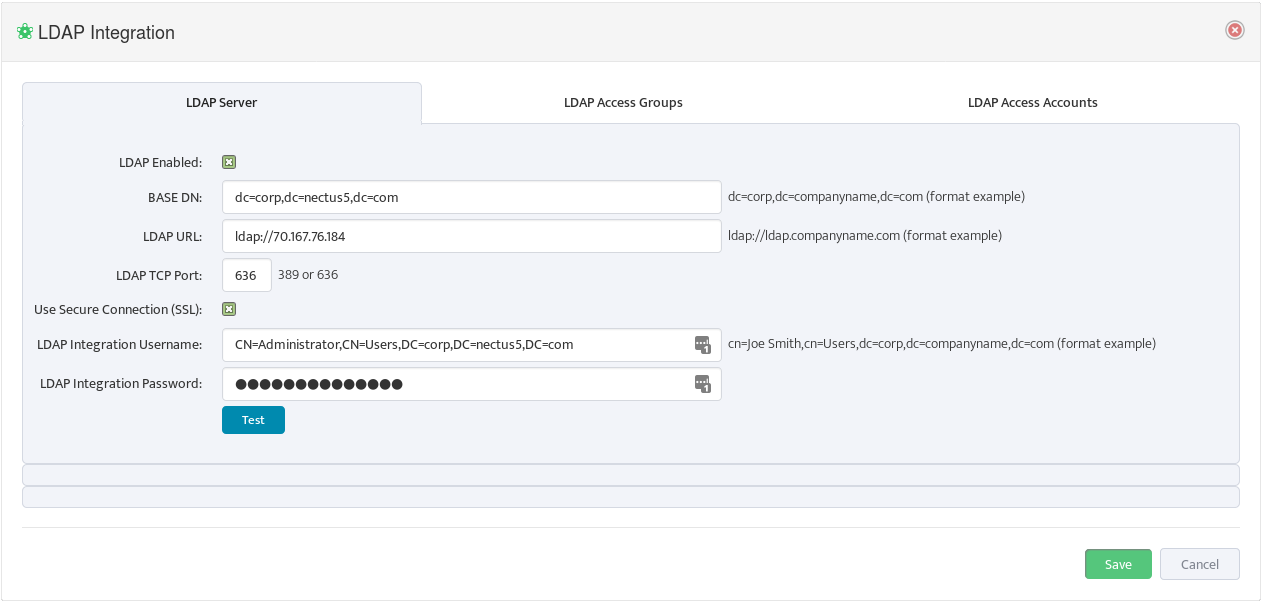
Select the LDAP Server tab and enter the LDAP parameters. You can see examples of the format for these parameters to the right of the relevant fields. Check LDAP Enabled.
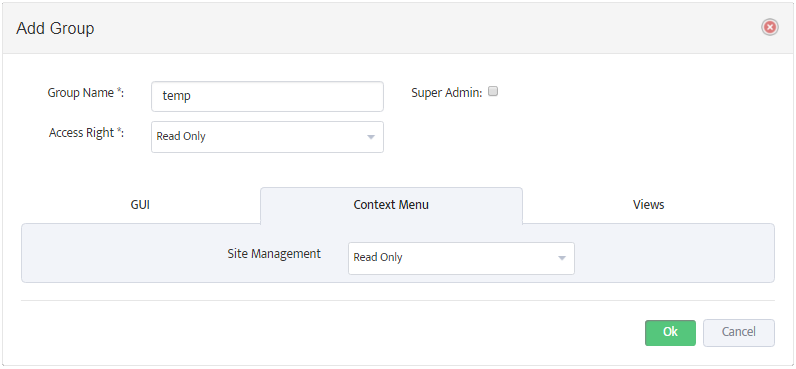
5. Mapping AD/LDAP Groups to Nectus Local User Groups
Mapping an AD/LDAP Group to a Nectus Local User Group causes the entire AD/LDAP group to inherit the security settings from the Nectus Local User Group.
To map AD/LDAP Groups to Nectus Local User Groups, open the “LDAP Integration” dialog box and select the LDAP Access Groups tab.
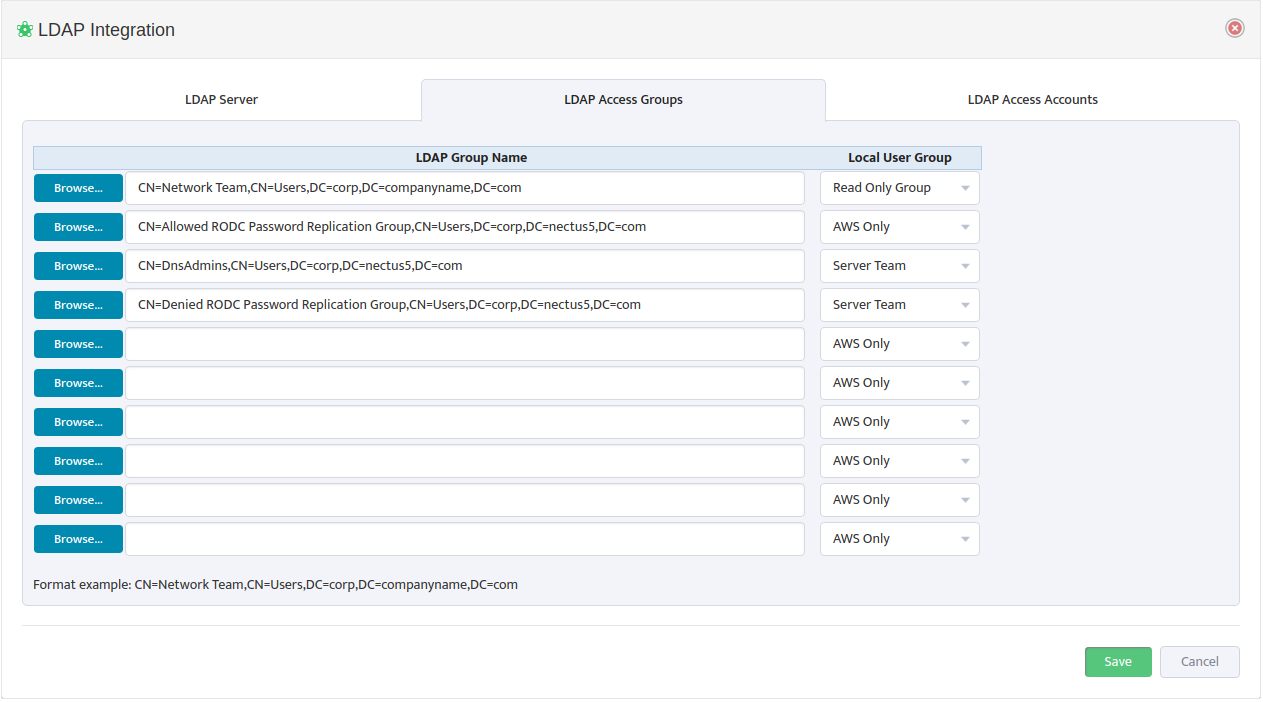
Use a Browse button on the left to open the “Select group from LDAP Server” dialog box and select an LDAP Group Name. 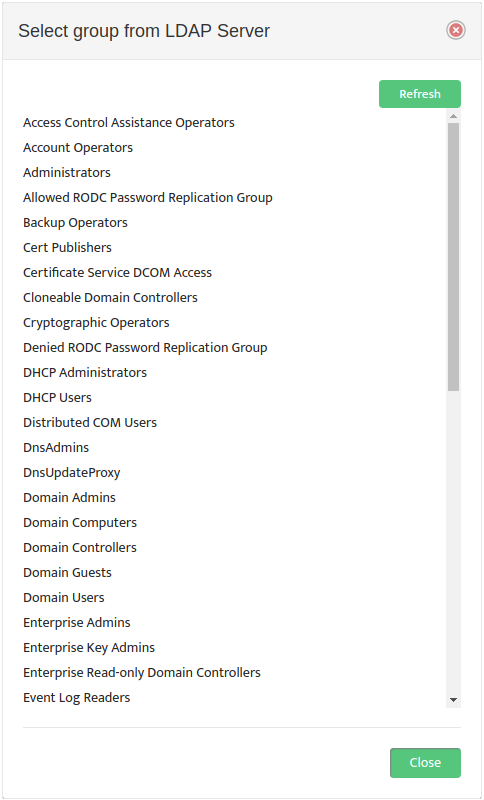
Nectus returns you to the “LDAP Integration” dialog box. In the drop-down list to the right of the LDAP Group Name, select the Local User Group to map it to. An example of the proper LDAP Group Name format appears at the bottom of the dialog box.
6. Mapping AD/LDAP Usernames to Nectus Local User Groups
Mapping an AD/LDAP Username to a Nectus Local User Group causes the specific AD/LDAP User to inherit the security settings from the Nectus Local User Group.
To map AD/LDAP Account Usernames to Nectus Local User Groups, open the “LDAP Integration” dialog box and select the LDAP Access Accounts tab.
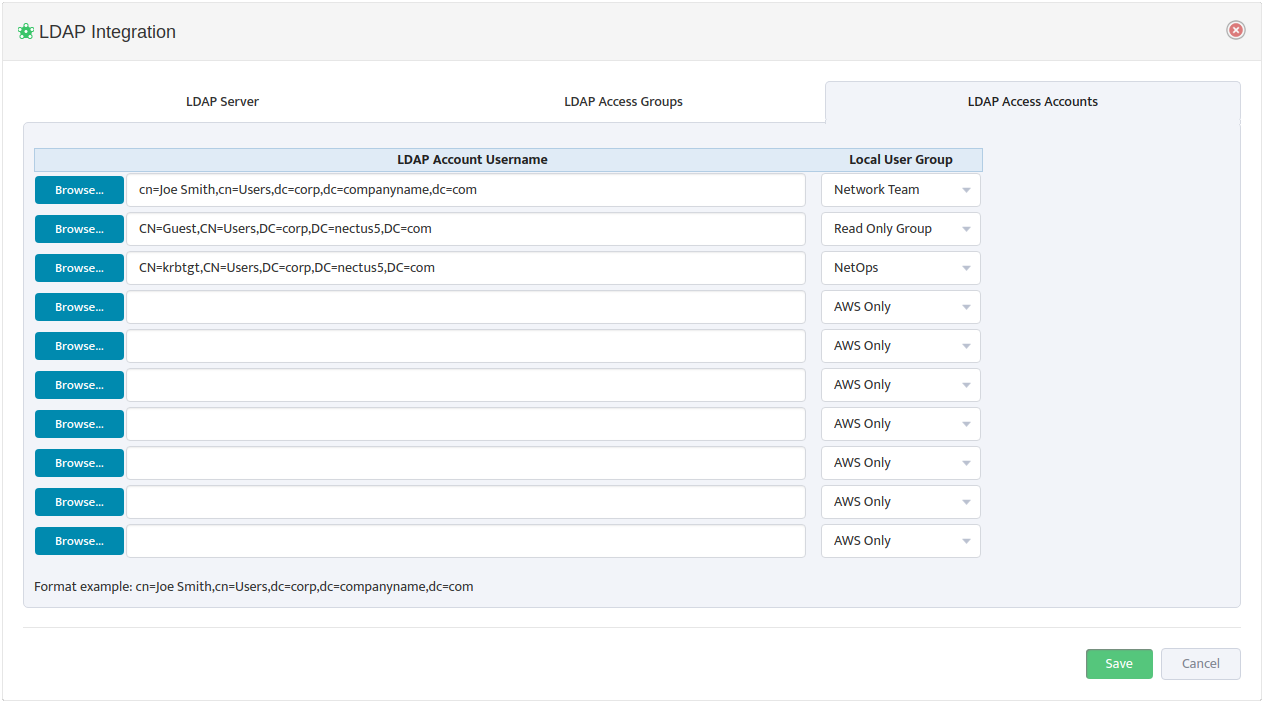
Use a Browse button on the left to open the “Select user from LDAP Server” dialog box and select an LDAP Account Username.
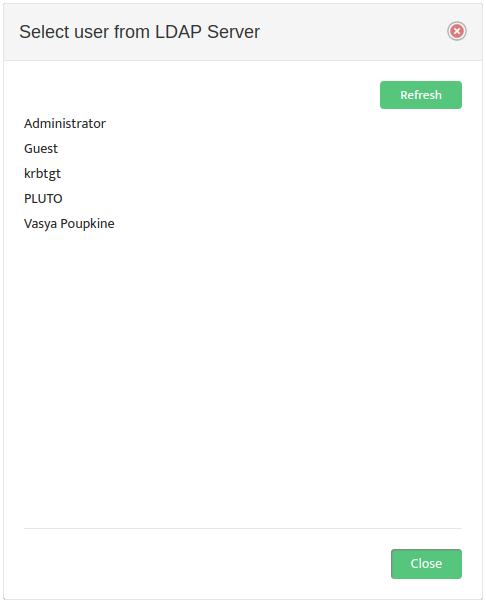
Nectus returns you to the “LDAP Integration” dialog box. In the drop-down list to the right, select the Local User Group to map the LDAP Account Username to. An example of the proper LDAP Account Username format appears at the bottom of the dialog box.